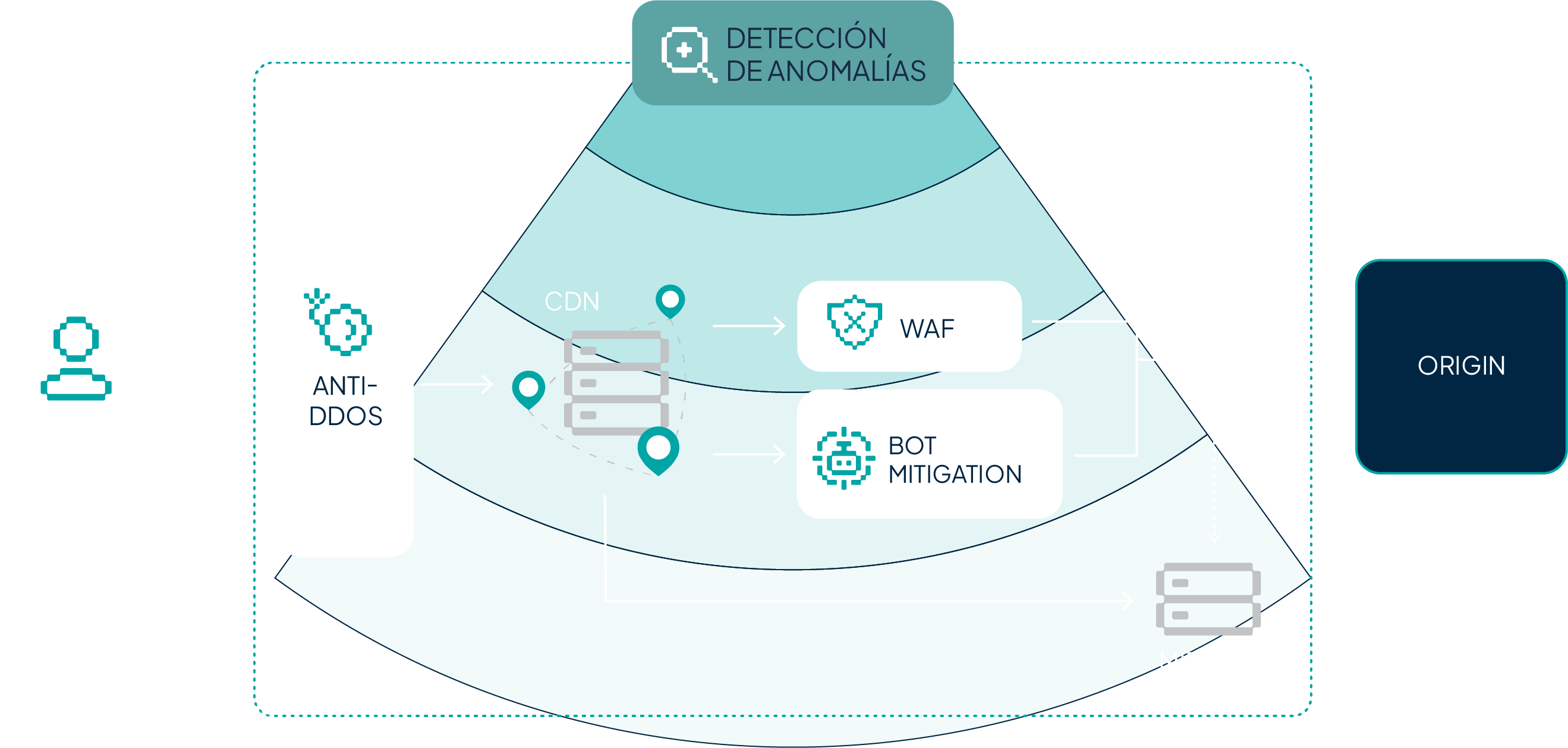
All areas of the IT ecosystem are exposed to a cyberattack to a greater or lesser extent. At Transparent Edge, we deal with hundreds of them on a daily basis, which allows us to develop different technologies for efficient threat detection and mitigation.
These features are unified in a complete and robust cybersecurity solution that protects your entire online business. With real-time visibility, precise controls, and the ability to stop the most sophisticated threats from a single platform. Free your team while shielding the security of your entire digital ecosystem.