Securing the web through edge computing

29 Oct 24

The rise of cloud computing presents major challenges for cybersecurity. With connected devices and distributed applications, the attack surface expands and new threats continually emerge. This context demands a more solid and multifaceted approach to protecting the web environment. In this post we explore how an edge cybersecurity suite can curb threats through the combination of different technologies.
Edge computing processes data closer to the end user, rather than relying on a single data center. That’s why edge cybersecurity solutions greatly improve the performance of a site by reducing the response time to a potential incident, expanding the scope of the solution, and containing threats on the nodes that are part of the platform, preventing access to the origin server.
As our CEO already mentioned in a previous post, we cannot expect a single tool to mitigate all types of attacks. Even more so in this context of change in which new hacking techniques are proliferating, increasingly sophisticated, multi-vector and extremely damaging.
It is therefore advisable to have different detection and response solutions. In the case of the web vector, for example, an Anti-DDoS that stops a volumetric attack by flooding HTTP/S requests at layer 7; but also a WAF that protects you from attacks that seek to exploit vulnerabilities in your code to steal data. The casuistry is endless.
Hiring different protection services requires a lot of resources, and not just financial ones, since the security team must deal with the analysis and management of a large amount of data from different solutions, platforms and providers.
This is where a cybersecurity suite makes sense, because it brings together different technologies in a single platform to minimize analysis and management tasks.
Our cybersecurity suite, which brings together advanced WAF, Bot Mitigation, Anti-DDoS and Anomaly Detection features, has been specifically designed to deliver these benefits, while also adding the ease of use that characterizes all our solutions. This means that any user, regardless of their technical knowledge, can understand the real-time analytics offered by our dashboard and respond to threats.
Perimetrical’s dashboard is designed to make the platform more user-friendly. It displays the main metrics in different diagrams so you can see at a glance what is happening on your site: requests, bandwidth, hit ratio, etc.
The data is displayed with different color patterns depending on the protection tool that reflects the information: green for WAF, blue for Anti-DDoS or maroon for Bot Mitigation, for example.
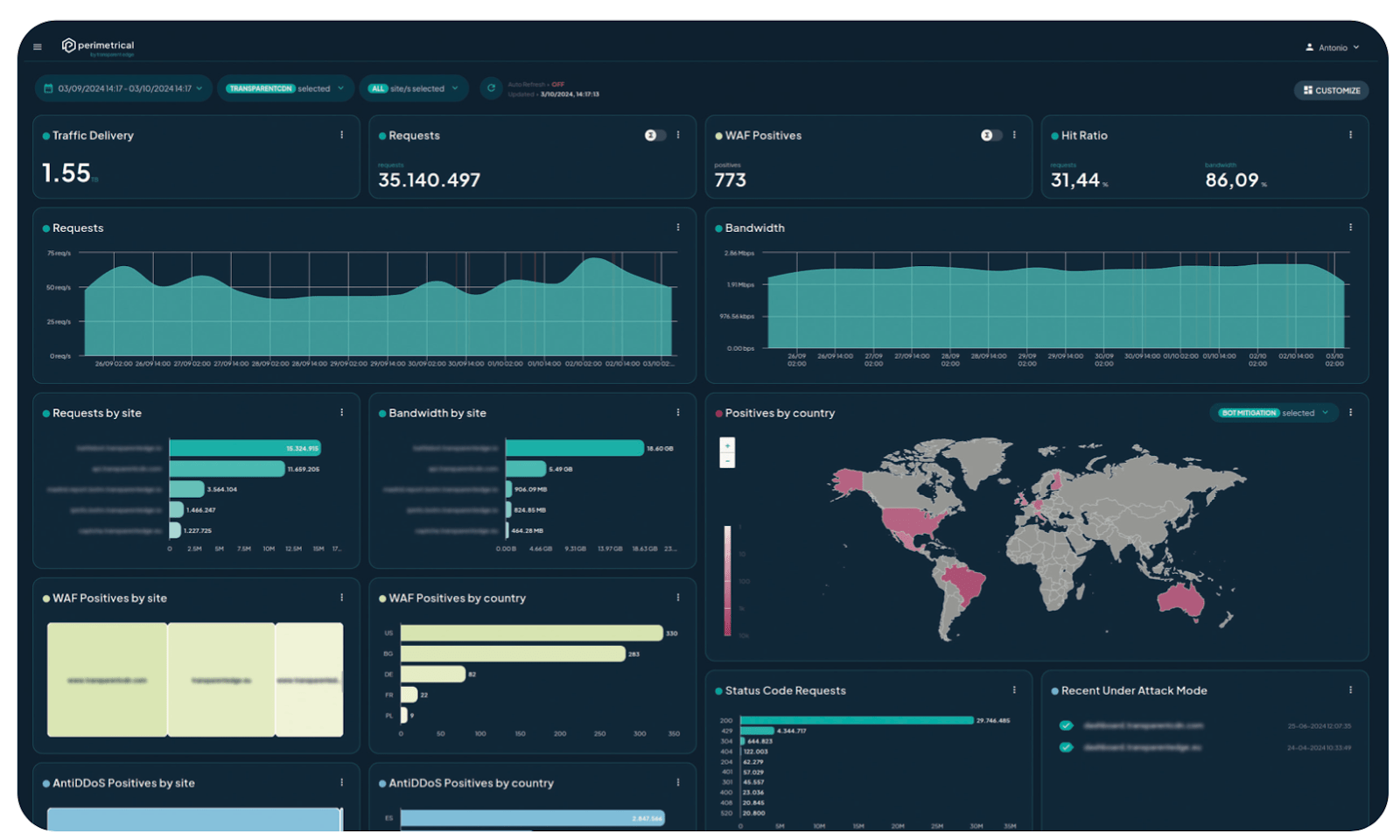
Additionally, widgets can be customized and a snapshot of the dashboard can be shared with other team members or our technicians whenever you need to verify a point.
This is interesting because no tool is 100% effective without a response team behind it. And ours is, in addition to being fast and proactive, also expert in the latest web protection techniques.
For example, a few days ago the team recommended to one of the aggregators we work with to point their DNS to our nodes to mitigate a origin denial of service attack they were suffering. Case solved ✅.
In the event of any fraudulent action that occurs in the web vector: a denial of service attack, a SQL injection attack, web crawling, etc., our team can propose different techniques to respond quickly and decisively.
Would you like to learn more about how to implement this suite in your organization? Contact us and we will explain how easy it is to integrate our technology into your infrastructure: without interruptions in your service and in a transparent way (just like us).