Protect your websites and apps with our UAM

24 Apr 24

Distributed denial of service (DDoS) attacks on corporate websites and applications are becoming increasingly common. These actions aim to overload the server where the website is hosted with false requests so that it becomes unable to respond to legitimate requests.
Before we get into the details of how the Under Attack Mode feature works, let’s explain what DDoS attacks are and why they are a constant concern for CTOs and corporate website administrators.
A DDoS (Distributed Denial of Service) attack is a malicious attempt to overload a web server with a large volume of traffic, with the aim of taking the site out of service.
The consequence of one of these cyberattacks is a poor experience for visitors, a drop in search engine rankings and the consequent possible financial and reputational loss.
The UAM (Under Attack Mode) feature acts as a protective shield for your website, mitigating DDoS attack attempts and excessive bot traffic.
Under Attack Mode is an on-demand command. It can be triggered either manually or automatically from our API and allows you to react quickly to an incident.
When Low Attack mode is activated, our system filters all traffic coming to your website or application by identifying and blocking any malicious or suspicious traffic, while allowing legitimate traffic to pass through without problems.
This helps keep your website accessible to your genuine users, while attackers are blocked.
It is also effective against excessive bot traffic, which can overwhelm your server and negatively impact website performance. This unwanted traffic can come from malicious bots or legitimate web crawlers that consume a lot of resources.
Transparent Edge uses a variety of advanced techniques to identify and mitigate DDoS attacks, such as analyzing traffic patterns, calculating average request rates, response time variation, and identifying malicious bots.
Enabling Under Attack Mode is very easy. Press the “Under Attack?” button on your dashboard and a pop-up window will open allowing you to select which of your sites is under attack:
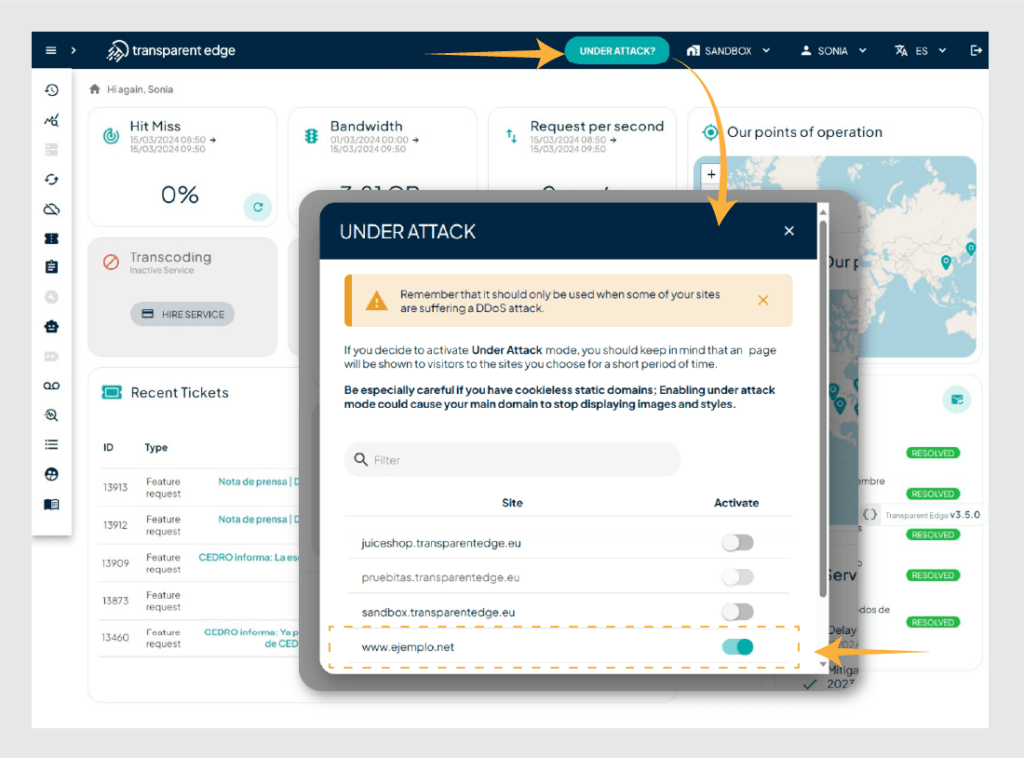
When you enable Under Attack mode, the visitor will be shown an interstitial page for a short period of time while the request is checked, and they can continue browsing without problems.
If you have the Anomaly Detection System, you can configure the detection parameters individually by customizing their threshold and sensitivity based on the nature of each website or API.
You can enable attack mode for specific ASNs, countries or IP ranges, URLs, domains… The configuration flexibility is complete.
Under Attack Mode is an essential tool to protect your website against DDoS attacks and excessive bot traffic. It offers robust and effective protection, without affecting performance for legitimate users.
You can keep your platform up and running and your business safe with Transparent Edge, as Under Attack Mode is included in all plans.
#secureYourSite