How to defend yourself from a cyber-attack or use a fork to eat soup

23 Jan 24

In a world as digitalized as ours, multiverses aside, cybersecurity is a term that no one is unaware of. To a greater or lesser extent, we are all exposed to being the target of a cyberattack. But is there any tool capable of mitigating any type of attack? Today I answer this question in this post (spoiler: no).
Every day we read news stories about cyberattacks on large public and private entities. Small businesses and even ordinary citizens are often victims of these types of situations. From a simple virus on your computer to the theft of your bank accounts, including the well-known ransomware.
Within a platform like Transparent Edge, specialized in protecting websites, we deal with hundreds of attacks on our clients’ sites on a daily basis. It is very common for them to think that having a certain tool can mitigate any type of attack, but unfortunately this is not possible.
I like to use the analogy of a fork. Just as you don’t use a fork to eat soup, you can’t expect a single tool to mitigate every type of attack on your website.
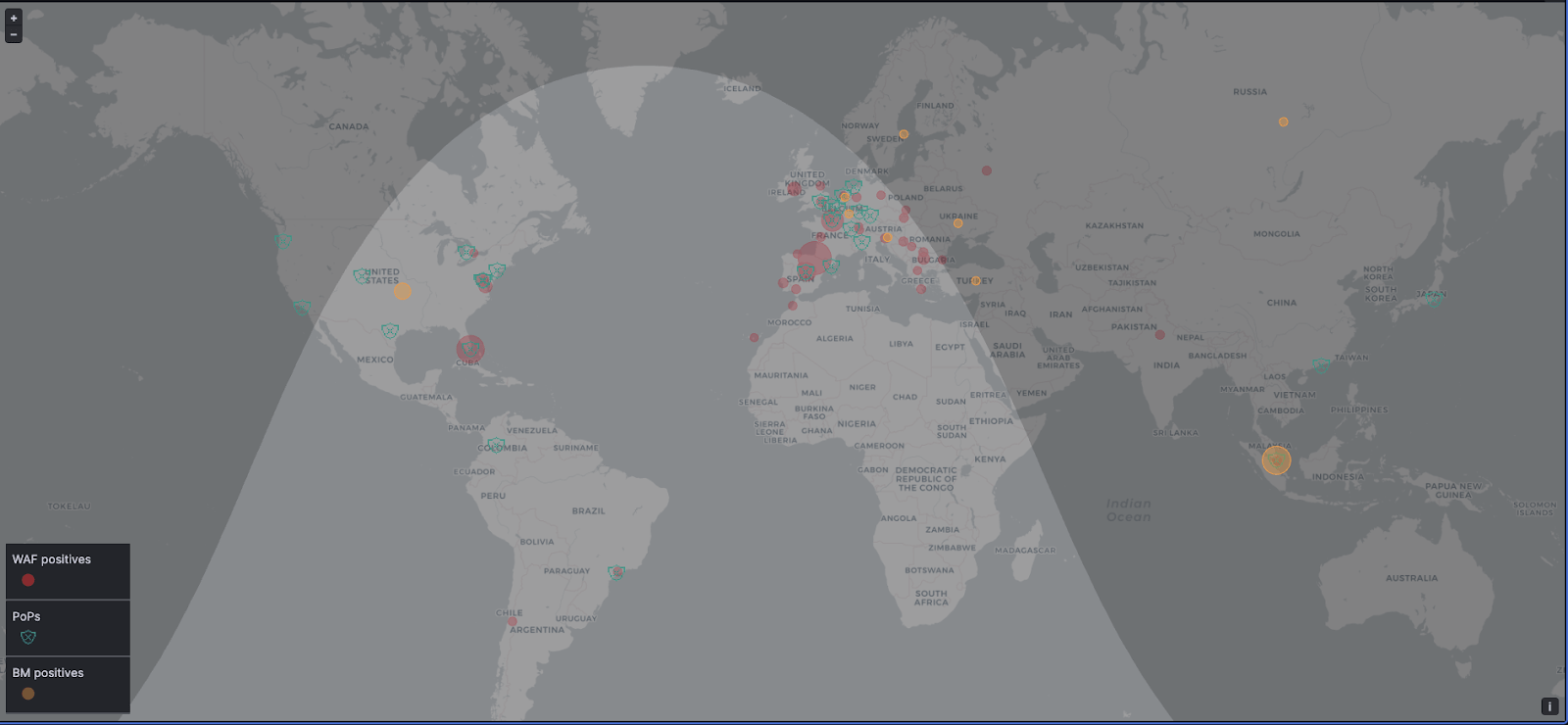
Along these lines, I usually make a very simple categorization based on the type of attack that your website may receive. On the one hand, we find volumetric attacks. These are the famous denial of service or DoS attacks, which can come from a single IP address or from multiple IP addresses (DDoS, Distributed Denial of Service) and which seek to take your website out of action for a certain period of time.
On the other hand, we find attacks directed at data. In these, the attacker will try to find a vulnerability in your systems, either in the code of your website or in the configuration of your server to steal information; or, compromise your server in order to control it for other purposes such as, for example, incorporating it into a botnet to carry out denial of service attacks or sending mass emails in the best of cases.
Continuing with the analogy, in this case that of the Swiss Army knife, in which you have your sharp knife to cut a rope or your screwdriver to get you out of a tight spot in the purest McGyver style, when it comes to protecting your website it is advisable to be prepared and have the necessary tools ready to stop any type of attack.
Anti-DDoS systems are tools that are usually activated on demand when you have detected that your website is under attack. There are usually two types, those that operate at the network layer (3 and 4) and those that operate at the application level (layer 7).
These types of tools help you mitigate a volumetric attack, where the attacker typically uses a botnet to simulate legitimate traffic to your website. The goal is to take it out of action and try to collapse the platform that serves your website.
I mentioned earlier that these types of tools are usually activated on demand, as they are usually intrusive elements and it is not advisable to activate them when you are not under attack. The reason is that you could prevent regular users of your website from accessing it. Although it is true that you can apply certain more lax measures as normal. These measures could be, for example, setting a rate limit that is “wide” enough to not harm legitimate users and restrictive enough to stop those malicious users who want to get under your skin.
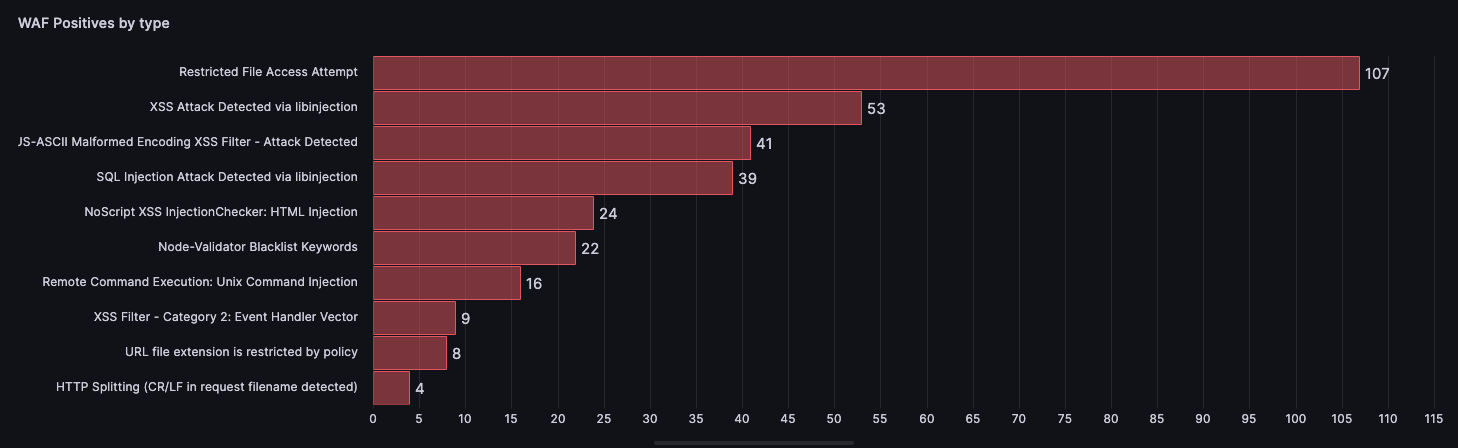
The WAF or Web Application Firewall is a tool that will protect you from those “lockpick” attacks, those that seek to exploit vulnerabilities in your code to steal your data or change the home page of your website to post messages and photos, which hacktivists like so much.
There are several types of WAFs, all of which are based on rules (and some would say AI). Some build them automatically and require a learning process where the WAF will try to figure out what is legitimate traffic and what is an attack. Then there are WAFs that already have a set of rules loaded. Both types analyze each request that arrives to see if it matches any of the rules that it has loaded and, if it does, it interprets it as an attack and the request is blocked and logged.
Many of the attacks mentioned are not carried out by humans directly, but rather use networks of compromised servers programmed to automatically attack their victims.
It must be said that not all bots are “bad”. Many perform tasks necessary for the correct functioning of the Internet, such as Google’s own bot, but it never hurts to know what they do, whether they are good or bad.
A May 10, 2023 report from Imperva claimed that nearly 47% of internet traffic comes from bot traffic. Not necessarily attacks, as I mentioned earlier, but it is a very high number that is, honestly, surprising.
Bot detection systems aim to detect non-human and potentially malicious traffic. These types of tools use different techniques, some of which are quite complex, to separate the wheat from the chaff.
Anomaly detection systems are systems that rely on data science to analyze patterns and detect anomalous traffic. For example, a sharp increase in requests per second or bandwidth on your website can be a clear sign that you are receiving a denial of service attack.
Having this type of system allows us to find out when something strange happens in our systems and to act accordingly, as quickly as possible. We can even respond to these events automatically, for example, by activating the Anti-DDoS system.
Finally, we cannot forget the human factor, which for me is the most important. There is no 100% reliable security system today, and if you are told otherwise, be suspicious. The reason is that all these types of tools are reactive and always lag behind hacking techniques that are constantly evolving. They are sticks in the wheels, as we always tell our clients, but they will undoubtedly make more than one hacker give up when they try to attack your website.
Along these lines, it is essential to have a team of experts who, when your website is under attack, will help you to adjust the necessary screws to mitigate it as soon as possible. And, of course, to gather all the required information in case it is necessary to report it to the State Security Forces and Corps.
Remember, the bad guys never sleep and an attack can come at any time, so it’s important to have people behind you who can respond 24×7.
Just as motorcycle enthusiasts say there are two types of riders: those who have fallen and those who are going to fall, in the world of cybersecurity we can also have our own version: there are two types of companies, those that have already been attacked and those that are going to be attacked again.
Jorge Román is co-founder and CEO of Transparent Edge.
Jorge Román is either a systems engineer who became a CEO over the years—or a CEO who became a systems engineer. He’s not entirely sure, and often thinks about it while mopping the office floor and serving coffee. The rest of the time, he runs the first CDN of Spanish origin, raises two daughters, and still finds time to read about entrepreneurship. As for sleep, he’s saving that for his next life.